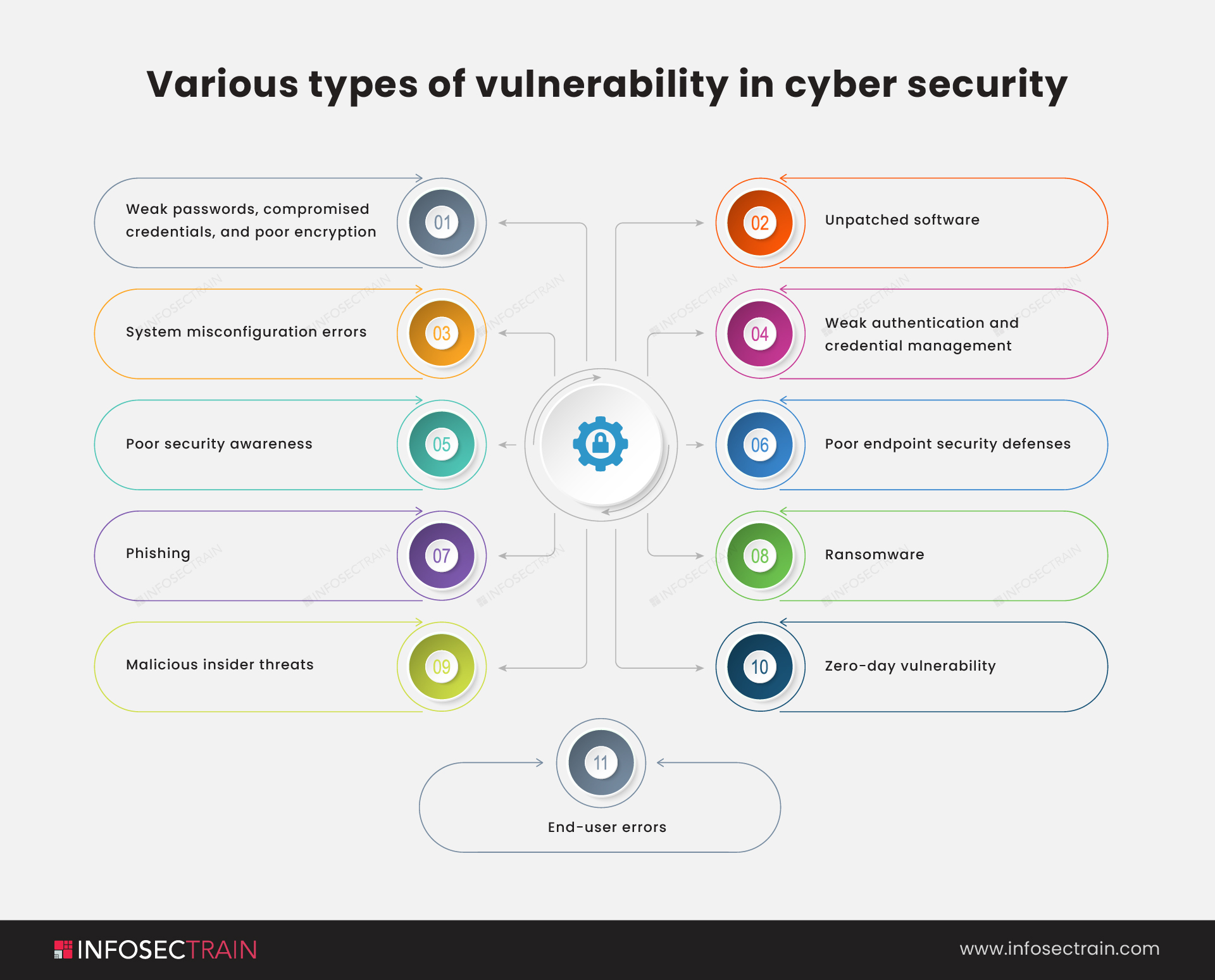
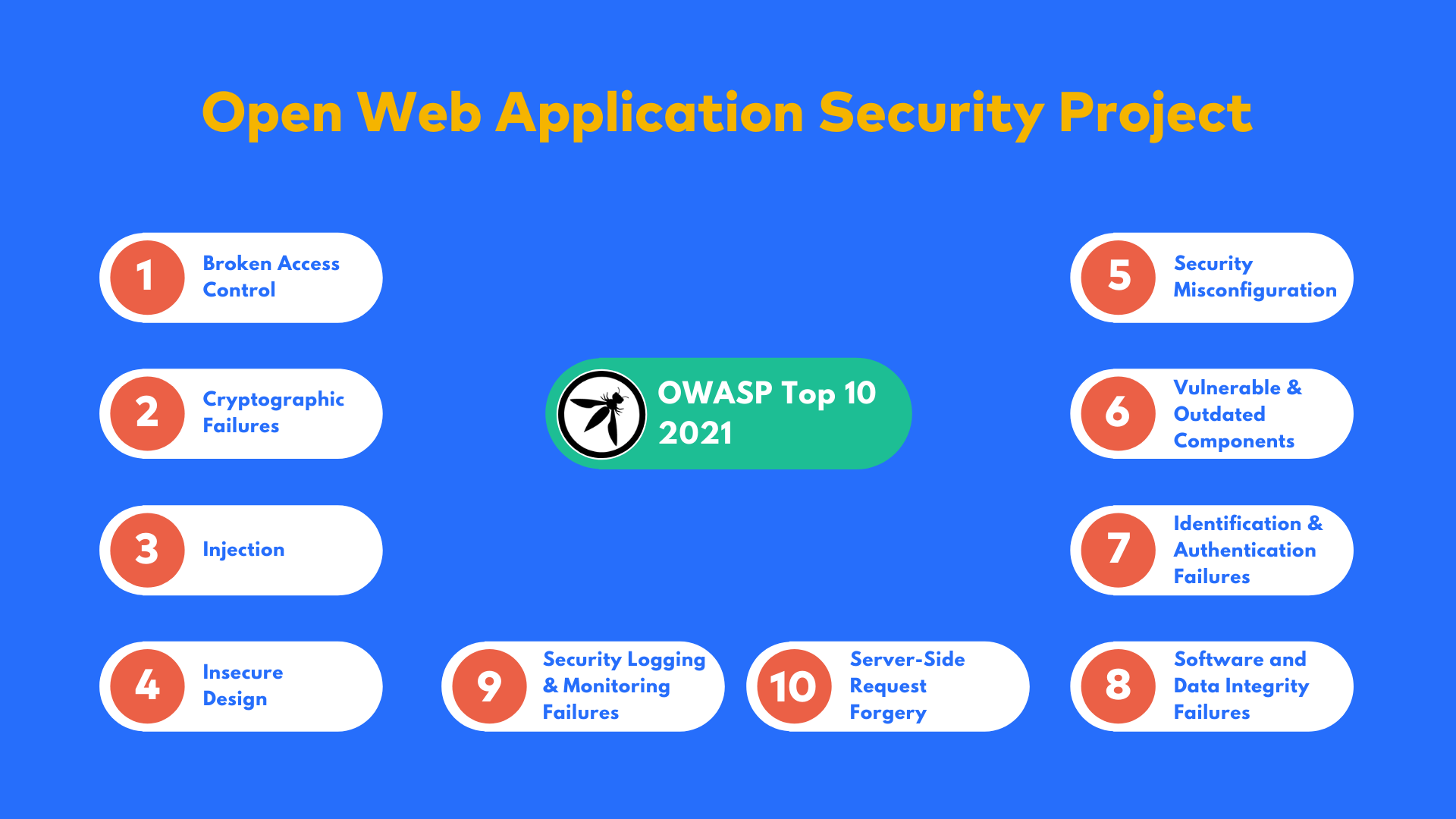
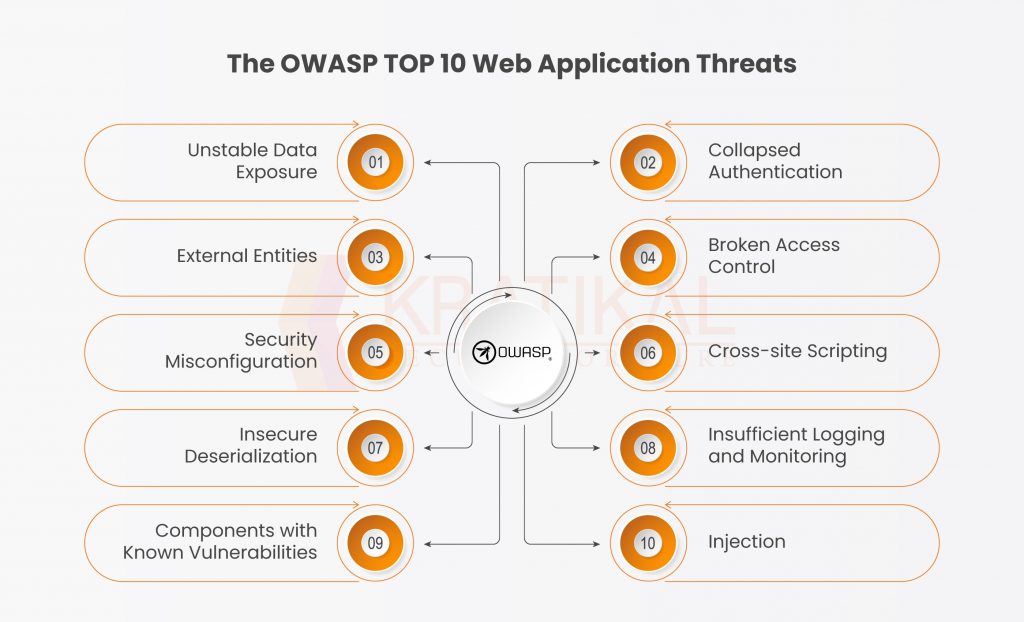
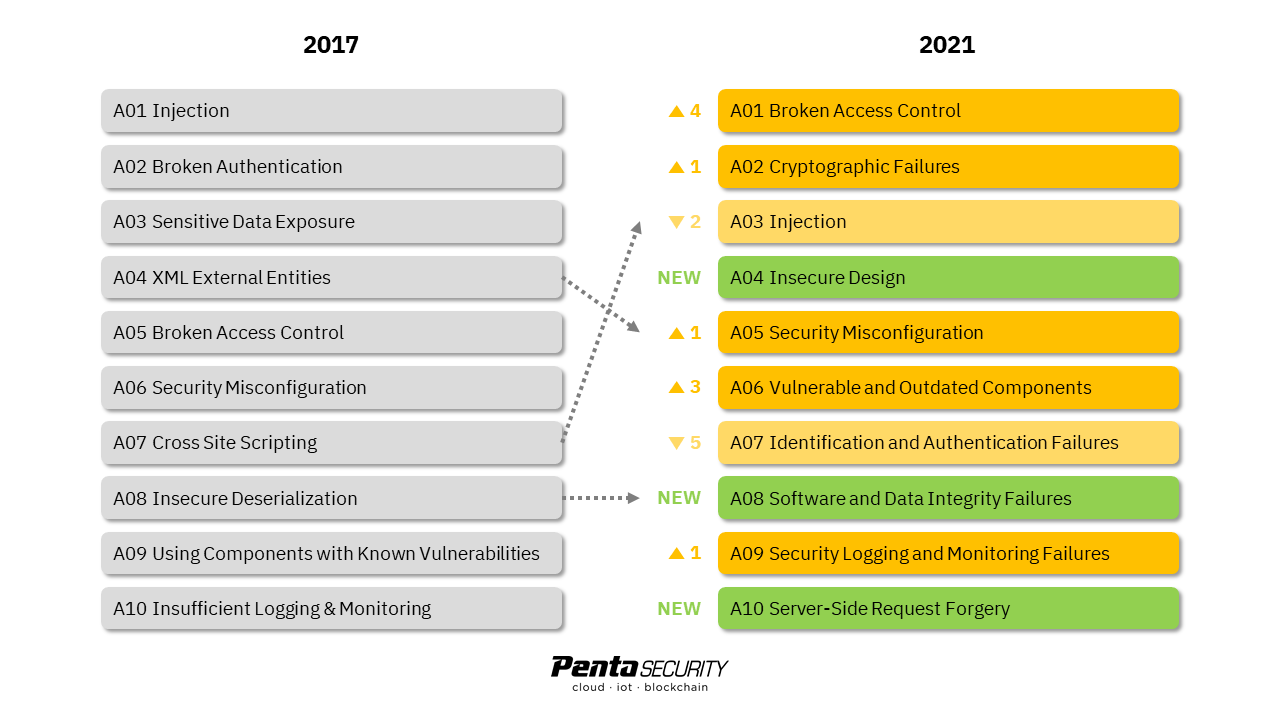
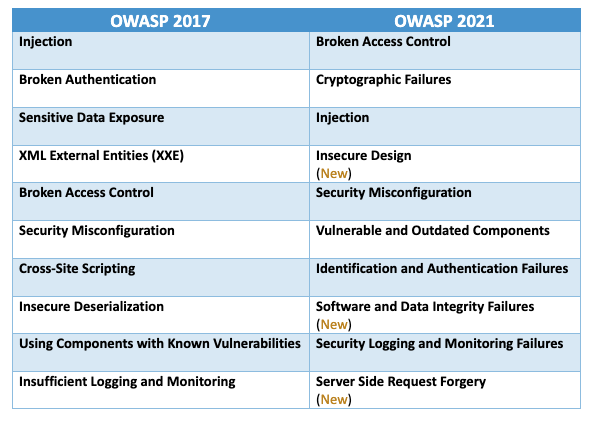
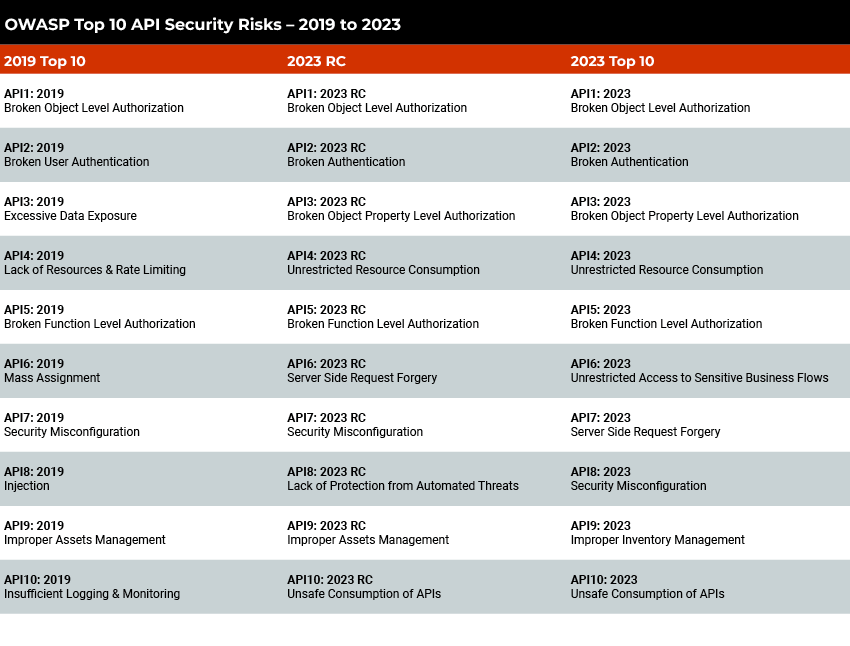
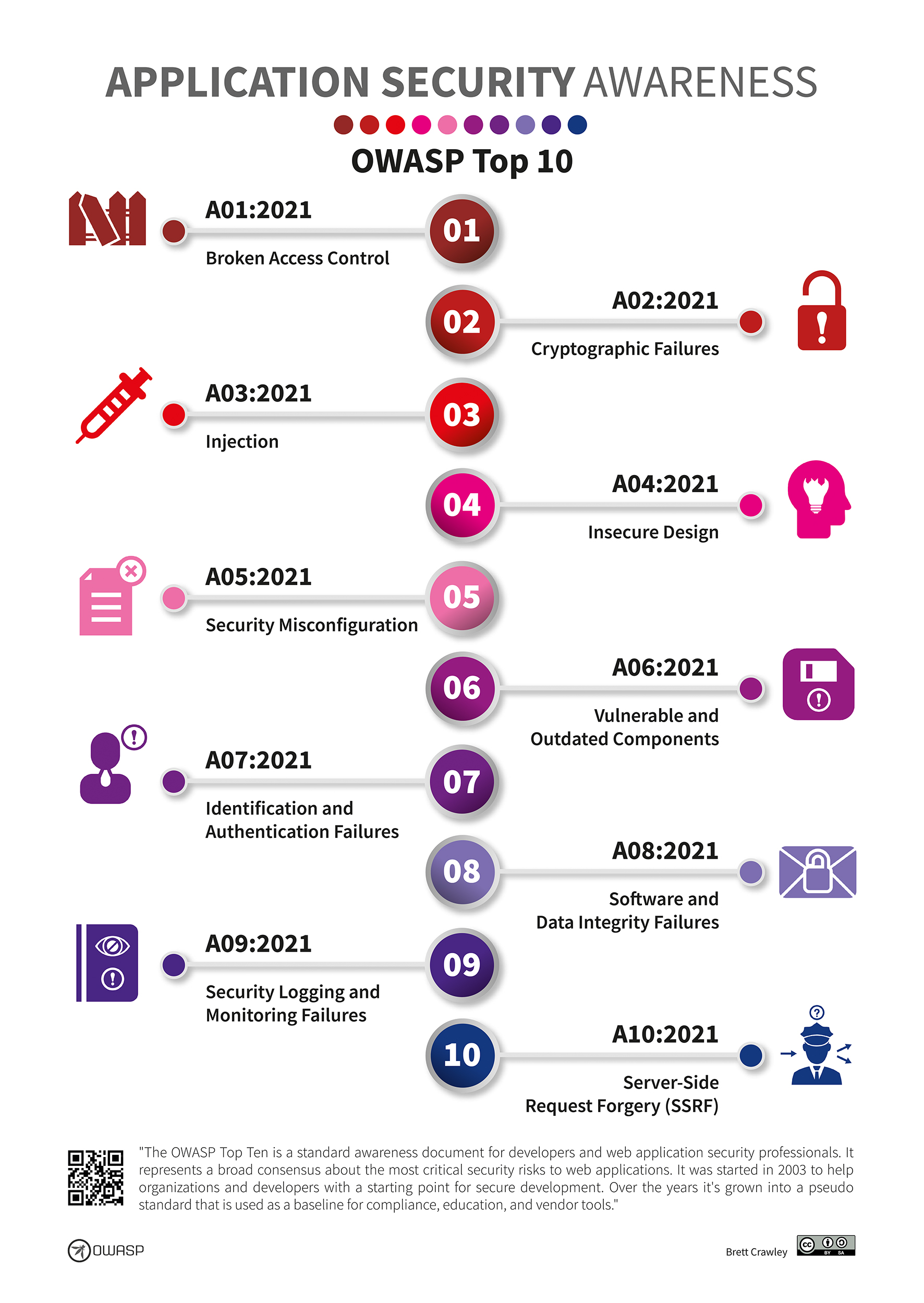
CyberCoE_Hyd on X: "Open Web Application Security Project (OWASP) is an international not-for-profit organization that maintains a rich collection of open source tools, training materials, and documents to help organizations identify, mitigate,
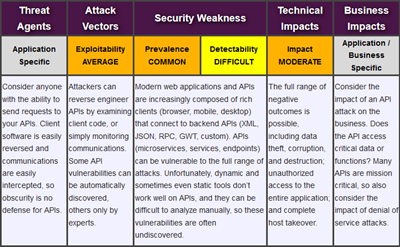
Prepare for the OWASP Top 10 Web Application Vulnerabilities Using AWS WAF and Our New White Paper | AWS News Blog

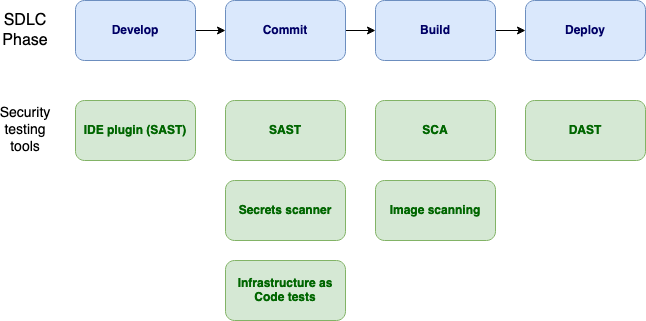
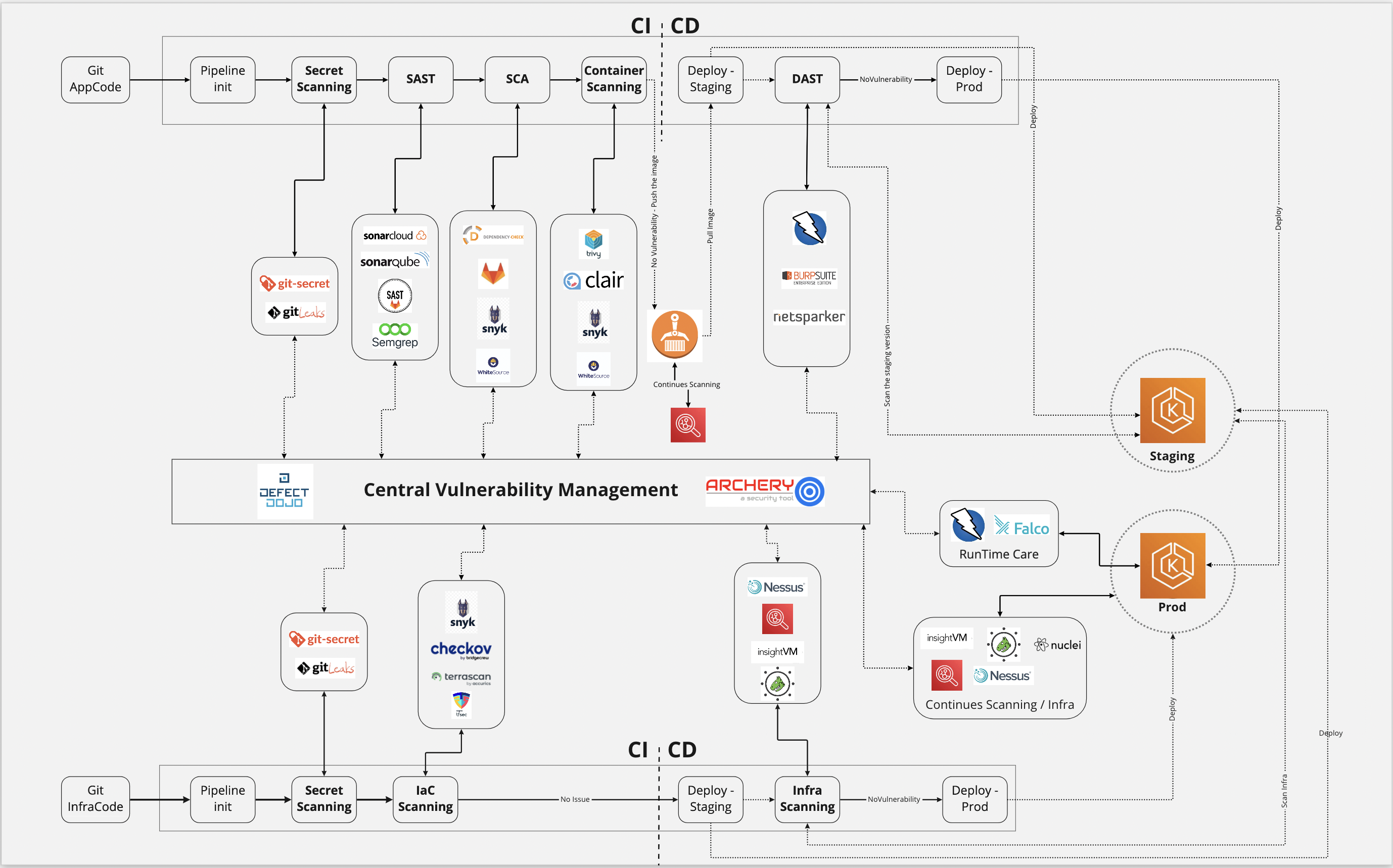
Enhancing Software Security: Leveraging OWASP Dependency-Check Scans for Proactive Vulnerability Management in CI/CD Pipelines | by Ramkrushna Maheshwar | Medium